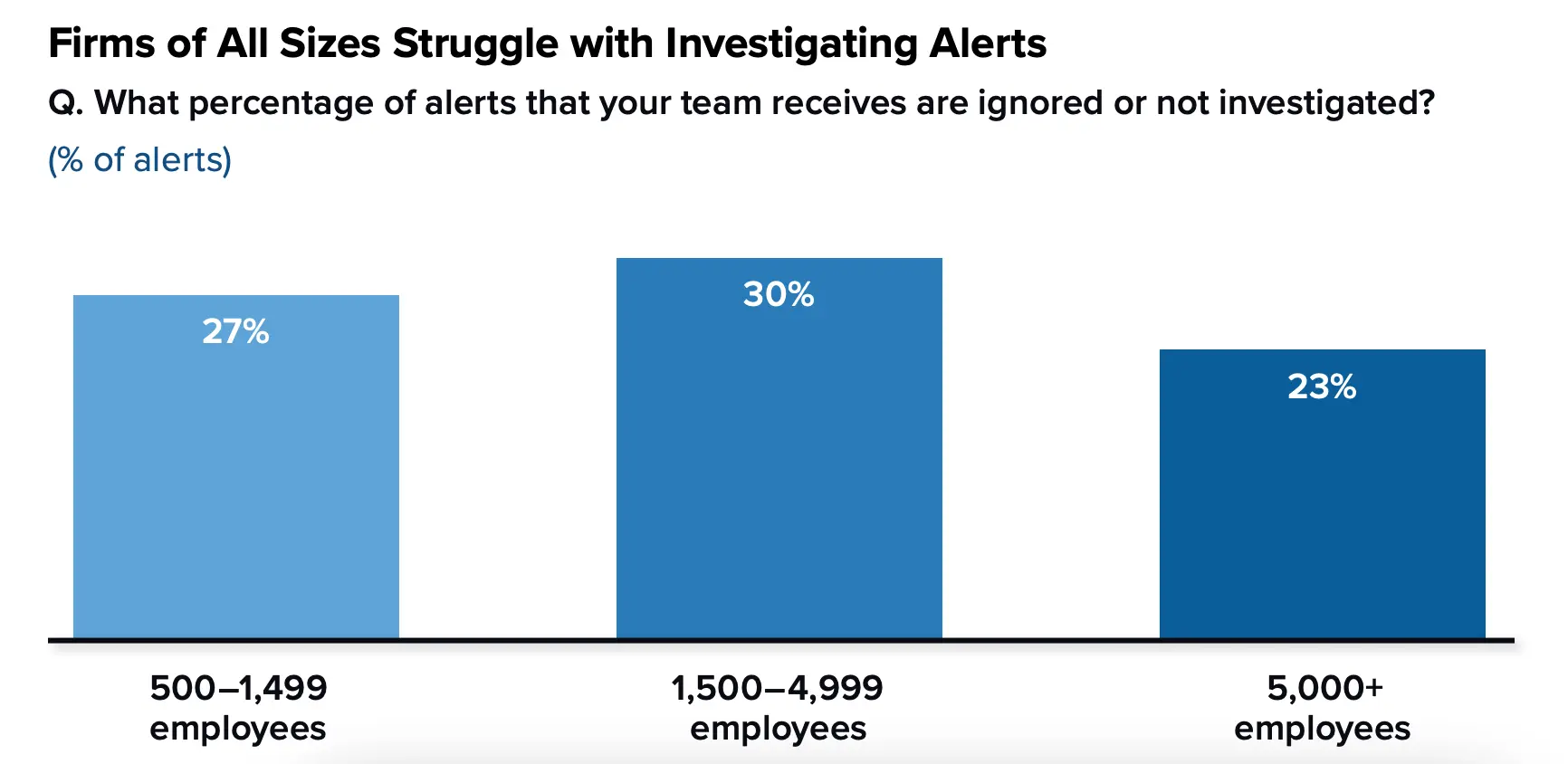
Security has become a paramount concern for organizations worldwide. The rising frequency and sophistication of cyber threats underscore the critical importance of robust security measures. Security is the backbone of IT operations, safeguarding sensitive data, critical systems, and the overall integrity of an organization. A security breach can result in severe consequences, including data breaches, financial losses, reputational damage, and legal ramifications. A recent report by IDC stated that companies of all sizes are ignoring one-third of security alerts and spending time investigating false positives.
As businesses increasingly rely on digital platforms and interconnected networks, the need for a proactive and comprehensive security strategy becomes even more crucial. So what’s the solution to make organizations secure? Let’s dig out the answer in this blog.
Why do Organizations Need Security Automation?
There are a number of reasons that can compel organizations to adopt, expand, and improve security measures.
- Unfortunately, for many organizations, the first indication of insufficient security measures often comes in the form of a security breach. According to research conducted by Splunk, within the past two years, 49% of respondents had faced a data breach, marking a notable increase from the previous year’s 39%. While some breaches may be minor and easily resolved, others can lead to substantial financial repercussions and even catastrophic outcomes. According to the IBM Cost of a Data Breach Report, the average total cost of a data breach reached $4.35 million in 2022.
- Security systems generate a lot of alerts daily, overwhelming IT teams. Distinguishing genuine threats from false positives is time-consuming and resource-intensive.
- Monitoring incident response times serves as an effective method to gauge the efficacy of your cybersecurity measures. When the mean-time-to-detect and mean-time-to-remediate incidents start to prolong, it signals a need for enhancements in your existing security infrastructure.
- Many organizations struggle with limited resources for security operations. This constraint can impede the ability to implement and maintain robust security measures effectively.
How Does a Security Automation Solution Help?
Automation emerges as a powerful solution to address the challenges faced by IT operational teams in maintaining robust security. By leveraging automation, organizations can enhance their security posture in several key areas:
-
Malware Detection
Security automation utilizes advanced algorithms and machine learning techniques to analyze patterns and behaviors indicative of malicious software. These systems continuously monitor network traffic, file systems, and application behavior to identify potential threats. They can detect suspicious patterns such as unexpected file modifications, unauthorized access attempts, or anomalous network activity. Once malware is detected on a network it isolates the host and network traffic access. Additionally, if it receives any alert from file systems, it instantly identifies the system, finds malware, checks the reputation, and detonates the file.
-
Incident and Event Management
Incident and event management streamline the entire lifecycle of security incidents, from detection and analysis to response and resolution. With automated security systems, the IT service desk can collect and correlate data from various sources, including security logs, intrusion detection systems, and network traffic analysis tools.
They can employ predefined rules and policies to identify suspicious activities and security breaches in real time. Once an incident is detected, automated workflows are triggered to initiate incident response procedures, including containment, investigation, and remediation. By reducing the time it takes to identify and respond to security incidents, automation minimizes the potential impact of cyber threats and helps organizations maintain operational continuity.
-
Data Exfiltration
Data exfiltration in IT refers to the unauthorized extraction or removal of data from a computer system, network, or organization’s environment. It occurs when sensitive or confidential information is intentionally or unintentionally accessed and transferred outside the intended boundaries of the system or network by an unauthorized entity.
Security automation here can monitor the data flows and communication channels and apply encryption and access control policies to prevent data exfiltration attempts. If an alert is raised, then the automated system can instantly block data transfer, disable the compromised user, and reset the password for the system. This way security automation reduces the risk of data breaches.
-
Alert Monitoring
With a lot of alert generation, IT service desk agents struggle to offer prompt service. Leveraging security automation, the IT service desk team can classify alerts based on their severity, relevance, and potential impact on the organization. Having security automation and AI in this process, service desk agents can resolve alerts for USB block/unblock, clean up requests for applications, and email alerts for account activation/deletion. Additionally, automation bots can perform on-demand checks for users who logged into certain workstations using their email or SMS.
-
Site Whitelisting and Blocking
Automation in site whitelisting and blocking enables organizations to control access to websites and online resources based on predefined policies and criteria. Automated web filtering solutions inspect URL requests, web traffic, and DNS resolutions to enforce site whitelists and blacklists. They categorize websites based on content, reputation, and security risk factors, such as malicious content, phishing attempts, or inappropriate material.
Is it Worth Using Security Automation?
Yes, In today’s intricate environments, security automation isn’t merely a luxury—it’s a necessity. With the proliferation of potential threats and cyber-attacks growing in both number and severity, highly skilled security professionals are scarce. Automation becomes essential in optimizing the job satisfaction and productivity of your top-tier security analysts by handling repetitive tasks.
Implementing security automation enables you to significantly slash incident investigation and response times, allowing you to stay proactive against emerging threats. Tasks that once consumed hours or days can now be completed within seconds. This accelerated response capability ensures swift threat mitigation and enhances customer protection, thereby safeguarding your organization’s reputation and financial well-being.
The post What is Security Automation? appeared first on AutomationEdge.
This is a companion discussion topic for the original entry at https://automationedge.com/blogs/what-is-security-automation/